Why SOC 2 Compliance Matters for Your Business

Every business, regardless of size or industry, collects vast amounts of data from its customers. For Shippo, such data could come from services such as facilitating shipping, creating labels, tracking shipments, address validation, customer support, technical services, etc. with the collection of such data and the rise in data breaches comes greater scrutiny around data compliance. This has led companies to meet new laws, regulations and compliance standards.
One of the compliance standards is SOC 2, adopted by Shippo in 2022. Shippo achieved its first ever SOC 2 Type 2 attestation in December 2022 by demonstrating to its customers and partners that it has implemented effective security controls to protect their data based on the trust services criteria relevant to security, confidentiality, and availability.
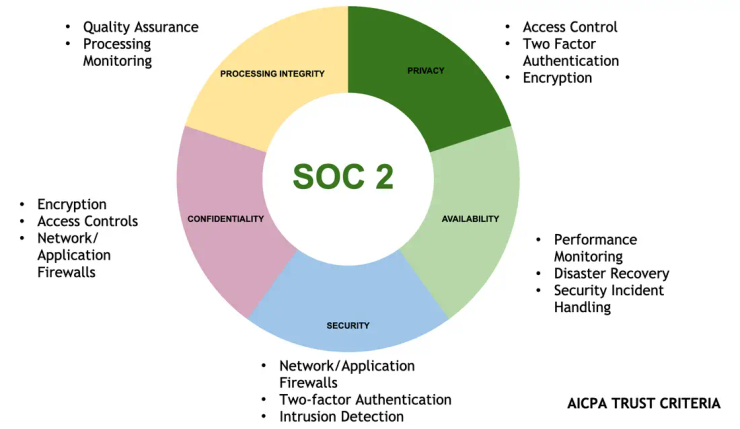
SOC 2 is based on the Trust Services Criteria (TSC) developed by the American Institute of CPAs (AICPA) that provides independent validation that information security systems are operating effectively and securely. The TSC includes five principles that companies must follow to achieve SOC 2 compliance: security, availability, processing integrity, confidentiality, and privacy. If you would like to gather more information on TSC, you can download the implementation guidance provided by AICPA
Shippo’s Journey to SOC 2 Compliance
The Journey towards SOC 2 Compliance was challenging but ultimately rewarding. Shippo began its journey in early 2022 by conducting a thorough risk assessment of its systems and processes to identify areas of weakness that need to be addressed. This helped determine which controls needed to be implemented. We designed these controls to address the TSC categories that applied to Shippo.
The control design phase where a third-party auditor examines the company’s controls and procedures to assess whether they meet the criteria set forth in the Trust Services Criteria (TSC) is also referred to as a SOC 2 Type 1 assessment . It is important to note that a SOC 2 Type 1 assessment provides a snapshot of the company’s control environment at a specific point in time.
Achieving a SOC 2 Type 1 helped Shippo to build the skills and practices necessary for ongoing compliance and showed its commitment to information security and privacy. Once a SOC 2 Type I assessment completed, Shippo embarked on its SOC 2 Type 2 journey by carefully planning and executing the requirements. A SOC 2 Type 2 assessment provides a more comprehensive evaluation of a company’s control environment than a SOC 2 Type 1 assessment where the external auditor evaluates the design and operating effectiveness of the controls to determine whether they are properly designed and working effectively over an extended period.

While planning for SOC 2 Type 2 assessment, below are some steps that were considered:
- Determining the assessment scope
- Conducting a readiness assessment
- Developing policies and procedures
- Identifying and engaging an external audit firm
- Conducting the audit
The external audit firm selected by Shippo audited its systems and processes to ensure it met the SOC 2 criteria. The audit involved a combination of interviews, document reviews, and testing of controls.
Below are some examples of common criteria control areas that were reviewed during the audit and expected to be implemented by Shippo.
Personnel Security:
- Annual security awareness training is required for all personnel; the training includes policy guidance on usage of confidential or personal information
- Confidentiality or other types of Non-Disclosure Agreements (NDAs) are signed by all employees and others who need to access sensitive or internal information
Secure Development & Secure Testing:
- Shippo has a formal systems development life cycle (SDLC) method that governs the development, acquisition, implementation, and maintenance of computerized information systems and related technology requirements
- External penetration tests are conducted annually, and vulnerability assessments are performed on an at least monthly basis, and management starts corrective actions for identified vulnerabilities
Cloud Security:
- We encrypt at rest and in transmission to prevent any unauthorized access
- Security monitoring applications are configured to alert IT personnel, such as via e-mail notification, when certain defined events have occurred
Do companies such as Shippo that offer both a shipping platform and API solution for E-commerce retailers, marketplaces, and logistics required to get SOC 2 compliance?
There is no regulatory requirement for Shippo to get SOC 2 compliance. However, many shipping e-commerce partner organizations have started requiring vendors to maintain cybersecurity certifications like SOC 2 as a result of the increased volume and severity of cybersecurity risk exposures.
SOC 2 examinations provide assurance that businesses are maintaining strong security and confidentiality controls and also serve as evidence that the entity has performed sufficient due diligence of permitting access to sensitive information and systems to any third parties.
Improved Security, Ongoing Compliance, and Customer Trust
It’s important to note that SOC 2 compliance is not a one-time event but an ongoing process of continuous improvement. There are many benefits to a business, and by maintaining a culture of security and compliance, any organization can demonstrate trustworthiness.

By successfully achieving its first ever SOC 2, Shippo is now able to provide assurance that it has a strong cybersecurity stance, assure customers that their data is secure, and show customers its commitment to security. As Mike Machado, Shippo’s Chief Data and Security Officer, states, “A good security posture helps companies do business with each other and makes partnerships easier and speed negotiations. Customers can do their due diligence for vendor risk management much faster. Therefore, SOC 2 cuts deal friction and our aim is zero deal friction”.
Shippo’s customers and partners can now request a copy of Shippo’s SOC 2 Type 2 report for their review upon execution of an NDA by either contacting the Support Team or the Sales Team. In addition, the Security, GRC & Trust team at Shippo can answer questions pertaining to Shippo’s SOC 2 controls.
If you are starting your SOC 2 journey, here are some tips that I wanted to share with everyone:
- Start early, embed processes and security controls into the company’s culture from the beginning.
- It is critically important that you understand your SOC 2 scope and the trust criteria you are planning to assess.
- Develop policies and procedures that align with current processes and address the control objective.
- It is a good practice to conduct an internal audit to assess your SOC 2 controls and address any gaps prior to the final assessment.
- Last but not the least, ensure all stakeholders are aware of the SOC 2 audit and buy into the process.













